Microsoft Cloud Application Security
RSA is the world’s largest cybersecurity conference and a key moment for the industry, which our product team has eagerly been working towards.Today we are excited to announce more than 15 new product capabilities for Microsoft Cloud App Security (MCAS).They are oriented around 4 major themes, as we continue to deliver a unique Cloud Access Security Broker (CASB) that is designed with security professionals in mind and continues to push industry boundaries by providing cutting edge capabilities, simplicity of deployment, centralized management, and innovative automation capabilities. State-of-the-art Threat ProtectionMalware poses risks to organizations and individuals in the form of impaired usability, data loss, intellectual property theft, and monetary loss. Microsoft uses a broad array of tools and techniques to identify, block, and eradicate malware infections wherever they are found. 1 As cloud threats continue to evolve, it is becoming increasingly important to detect not only known, but especially zero-day, malware that is infiltrating your cloud environments.UBA enhancements and User Investigation PriorityBy integrating with the Microsoft Intelligent Security Graph, MCAS has an unparalleled view into the evolving threat landscape, enabling us to continuously evolve our detections and enhance our UBA capabilities. At the same time, we recognize that prioritization is key for often understaffed SOC teams. That’s why we have added a new, powerful investigation priority for users, based on the new.
It provides admins with an overview of the users who likely pose the greatest risk to the organization and are recommended for immediate review. It takes into consideration several conditions such as the type of alerts, as well as a user’s overall impact to the organization, e.g.
Their level of access to sensitive information, based on patented UBA mechanisms.Image 1: The new User risk overview provides you with User Investigation Priority and timeline of suspicious alerts and activitiesMalware DetonationMicrosoft Cloud App Security is introducing malware detonation capabilities for our API-connected cloud storage apps. Intelligent heuristics allow us to identify potentially malicious files, rather than needing to detonate all files, to minimize the impact on user productivity. Once a suspicious file has been identified, it is then detonated in a sandbox environment and alerts the admins. Malware investigation and detonation is automatically applied to newly uploaded files in near-real time, as well files that already exist in your connected cloud apps.Adaptive DLP ControlsHackers want information.

More organisations than ever are adopting SaaS applications as standard. Not only does this reduce IT costs, but SaaS apps enable organisations to deliver products and services faster to market with improved internal collaboration.With the significant rise of unsanctioned Shadow IT in recent years, your users may be using cloud applications you are not aware of to share sensitive corporate data. With such a fast transition to cloud apps, you may be concerned about storing your corporate data in the cloud, making it accessible to users anywhere.
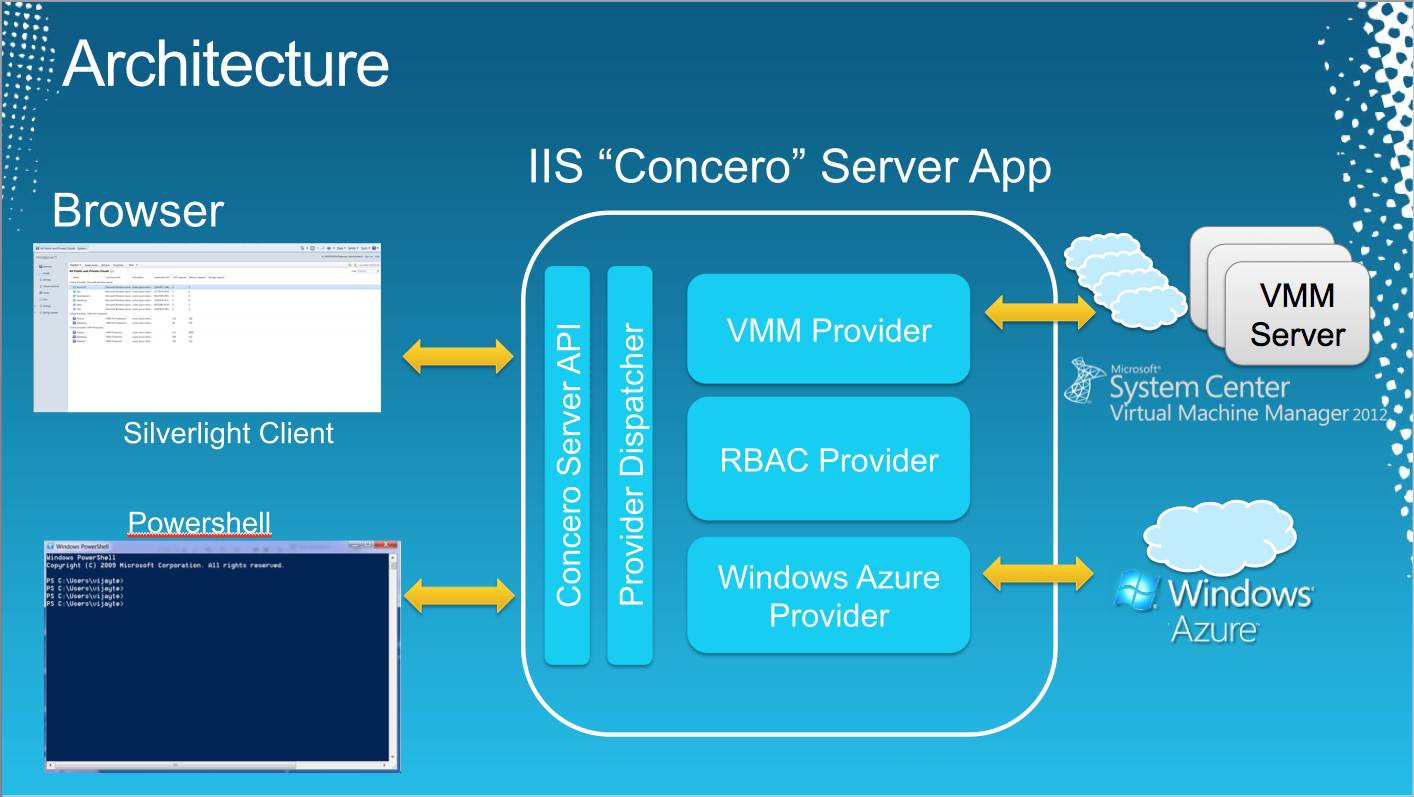
Cloud App Security
Microsoft Cloud Application Security Portal
With the impending GDPR legislation, having the ability to protect and classify employee and customer data is now imperative. With AIP, an organisation can 1) classify the personally-identifiable information (PII) that GDPR seeks to protect, and 2) provide the technical controls to limit data loss risks.The classification and labelling capability provides the foundational demonstration that your organisation knows how to find your PII, and the protection capability provides encryption and rights enforcement to protect against unwanted or malicious leakage. GDPR introduces significant statutory fines for non-compliance, and we also know that many of the risks that GDPR speaks to carry significant intrinsic costs.How will the GDPR legislation affect your organisation?